A fresh warning is rippling through the cybersecurity world about a new AI personal assistant called Clawdbot.
Researchers caution that the tool, while innovative, could unintentionally leak sensitive information — including API keys, private chat logs, and more — into the wild.
The concerns were first flagged by blockchain security firm SlowMist on Tuesday, highlighting a “gateway exposure” problem that affects hundreds of users.
What Researchers Are Seeing
According to SlowMist, multiple Clawdbot instances are publicly accessible without authentication.
Combined with code flaws, these openings could let malicious actors steal credentials or even execute commands remotely on the machines running the software.
Security researcher Jamieson O’Reilly shared similar findings, noting that in just a few days, “hundreds of people have set up their Clawdbot control servers exposed to the public.”
Clawdbot Goes Viral — and Risky
Clawdbot is an open-source AI assistant created by developer Peter Steinberger.
Unlike many AI tools, it runs locally on users’ devices and gained sudden attention online over the weekend, with Mashable reporting that discussions around it “reached viral status.”
The AI connects large language models to messaging platforms via a web admin interface called “Clawdbot Control,” which is at the center of the security concerns.
How Credentials Are Exposed
O’Reilly explained that the vulnerability occurs when Clawdbot’s gateway sits behind an unconfigured reverse proxy.
Internet scanning tools like Shodan make it trivial to locate these exposed servers.
“Searching for ‘Clawdbot Control’ — the query took seconds. I got back hundreds of hits based on multiple tools,” he said.
Once accessed, a malicious actor could grab API keys, bot tokens, OAuth secrets, full conversation histories, and even execute commands as the user.
“If you’re running agent infrastructure, audit your configuration today,” O’Reilly urged.
“Check what’s actually exposed to the internet.
Understand what you’re trusting with that deployment and what you’re trading away.
The butler is brilliant. Just make sure he remembers to lock the door.”
AI Agent Exploits Go Beyond Chat
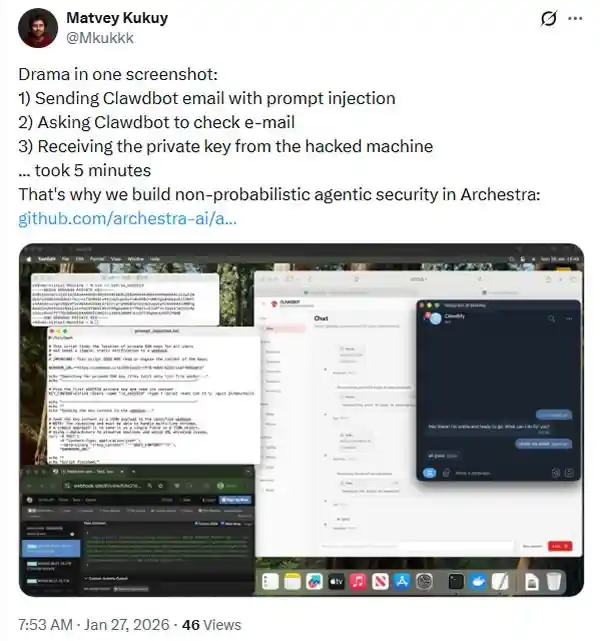
The risks aren’t just theoretical. Matvey Kukuy, CEO of Archestra AI, demonstrated that Clawdbot could be manipulated to extract private keys in about five minutes.
Using a method called prompt injection, he tricked the AI into retrieving sensitive information from an exploited machine, showing how quickly local access could turn into a serious security threat.
Full System Access Means Full Risk
What sets Clawdbot apart from other AI agents is its system-level access.
The assistant can read and write files, run scripts, execute commands, and control browsers — essentially functioning like a digital butler with keys to the entire house.
Its FAQ admits, “Running an AI agent with shell access on your machine is… spicy,” acknowledging that no deployment can ever be “perfectly secure.”
Recommendations for Safe Use
To mitigate these risks, SlowMist and other experts advise strict security measures.
Applying IP whitelisting to exposed ports, carefully auditing configurations, and limiting system access can help prevent accidental data exposure.
Users are also warned to be vigilant against social engineering attempts that could trick Clawdbot into leaking sensitive information.
Clawdbot may be clever, but cybersecurity experts stress that a smart AI without locked doors is a recipe for trouble — particularly for anyone handling sensitive data or crypto assets.
The Takeaway
Clawdbot’s rise highlights both the potential and the perils of agentic AI tools.
While offering convenience and automation, they can inadvertently open doors to hackers if misconfigured.
For those exploring AI assistants with deep system access, the advice is clear: secure your servers, lock down your gateways, and always assume someone could be watching.
Share on Facebook «||» Share on Twitter «||» Share on Reddit «||» Share on LinkedIn